Author

Arjan Neef
Testing, research and development
Bad configuration and remote code execution
After numerous failed attempts trying to inform a company that all its documents are out in the open I am out of clues. They just don't act on the information presented to them. Since it's a company documenting property values I though they might be more careful with the information. Client information, email accounts, property documentation it's all there. But we all make mistakes right?
In this article you can read about the steps I took and hopefully understand that ignoring serious warnings isn't a wise course of action. No, I will not name the company or disclose any vulnerable information to harm the company.
How I discovered the vulnerable website
If you've read my previous articles you can see I'm using a (self written) website scanner. What it does is use the dictionary and use all words to see if there is a website linked to it. It's currently still running but I can share some results of the scanner. What you see in the next image are all countries that have been scanned and ranked by cybersecurity. Green countries are generally better protected to malicious hackers than red countries.
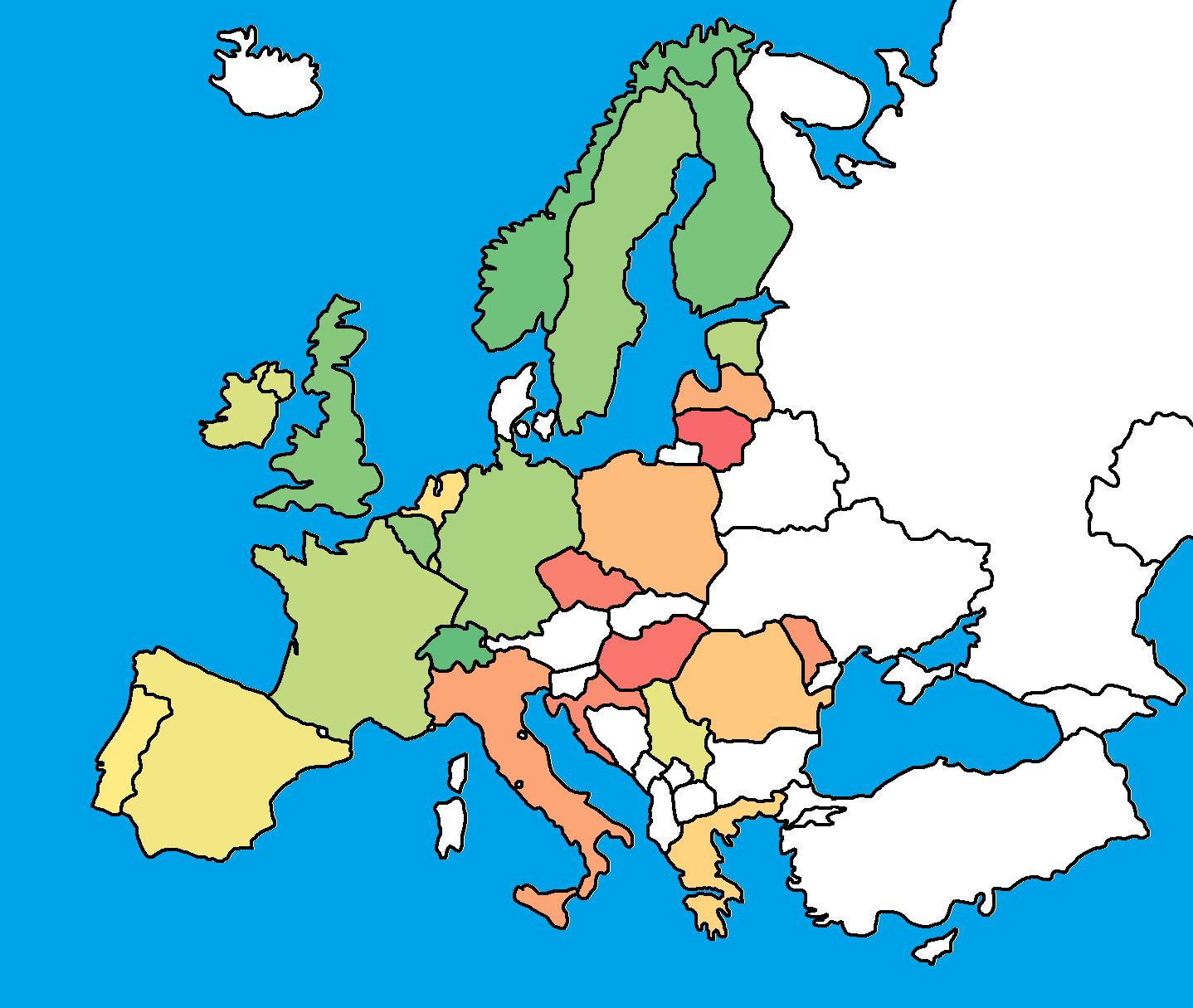
To use the scanner properly I've downloaded many different language dictionaries to match the scanner to words of the country. As you can see not all countries have been processed yet. To generate this image the total website counter is above 1 million different websites. More websites, more accuracy.
Living in a country that scores good doesn't necessarily mean that your website is good, it's just an average. Each website is analysed on the following items:
- Does it have the latest updates
- Is it a secure connection
- How well is the webserver configured
This gives me a list of websites ranked from good to bad based on cybersecurity. The company I'm referring to in this article ranked quite bad so I decided to take a closer look at the website to see what I would find.
First inspection
First thing I noticed was that the website supports both secure and insecure connections (HTTP and HTTPS). Normally HTTP traffic is redirected to the secure HTTPS connection but this website didn't do that. I also noticed that the (insecure) homepage of the website was rerouted to another location on the server by adding a new path to the URL. It looked like this:

Notice the name "subfolder" added to the website, that is done by the webserver. It also redirects to a login.php file used to gain access to the website. It's not that hard to remove the login.php to see what you get. And in this case it showed me the contents of the entire folder. Image is just an example, based on what I found.
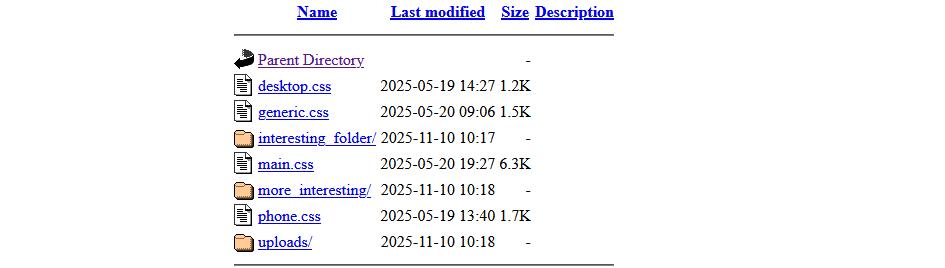
Here the uploads folder is very interesting, and when going through that folder I found lots and lots of interesting information that the company probably doesn't want to share with the whole world. So I decided to email the company to tell them their information is out in the open. I added some proof from their website so that they could realise it's not a fake email. Nothing was done, nor did they respond to my email. I tried to reach out to other people of the company too but decided to leave it there. It's not my responsibility. I think I tried to reach out to three different people. They would probably think my messages are scam?
Occasionally I revisited the website and saw more documents being added to the upload folder indicating the company is still active. I decided to take a closer look at the other accessible directories. In those folders I really found valuable information such as error logfiles and files showing limited database information. This information contains actual email addresses and account names. I really thought this was bad so I tried to reach out to the company once again but no result at all. I found other email addresses that were used outside the company but belonged to the same people so I tried to reach them there too. I thought that they might wonder how I got hold of those email addresses to create some extra alert awareness. But again no such luck.
After looking at the error logfiles I noticed that there is some sort of test account with a very short name. I tried to use this account and used the password matching the account name and it actually worked. This was a wild guess but I was able to login! Unbelievable. Not only that, this account allowed me to upload files too. Since I already knew where the uploaded files would be placed I uploaded an executable to see if this would work. Well,... yes, this also worked. So now I have control on their machine if I want to. But I want them to upgrade their cybersecurity. What a dilemma.
With this access I was able to add a small image to their website and tried to send another email once more. But again.... nothing changed. I guess some companies just never learn and will eventually be hacked by the wrong one. It's just a matter of time. I guess they don't refresh their browser to load the new images. If you don't notice I changed the logo of your website? (Just refresh your browser on the insecure website)
As a last result I send this article to the company but I guess nothing will change as they just don't understand cybersecurity. And most frustrating of it all is that the solution to their (yet unknown) problem is so very easy.





